Exam Code: 300-210 (), Exam Name: Implementing Cisco Threat Control Solutions (SITCS), Certification Provider: Cisco Certifitcation, Free Today! Guaranteed Training- Pass 300-210 Exam.
Also have 300-210 free dumps questions for you:
NEW QUESTION 1
What is a valid search parameter for the Cisco ESA find event tool?
- A. Envelope Origination
- B. Envelope Type
- C. Message ID
- D. Download Type
Answer: C
NEW QUESTION 2
With Cisco AMP for Endpoints on Windows, which three engines are available in the connector? (Choose three. )
- A. Ethos
- B. Tetra
- C. Annos
- D. Spero
- E. Talos
- F. ClamAV
Answer: ABD
Explanation: http://www.cisco.com/c/en/us/products/collateral/security/fireamp-private-cloud-virtual-appliance/datasheet-c780.html
NEW QUESTION 3
The security team needs to limit the number of e-mails they receive from the Intellishield Alert Service. Which three parameters can they adjust to restrict alerts to specific product sets? (Choose three.)
- A. Vendor
- B. Chassis/Module
- C. Device ID
- D. Service Contract
- E. Version/Release
- F. Service Pack/Platform
Answer: AEF
NEW QUESTION 4










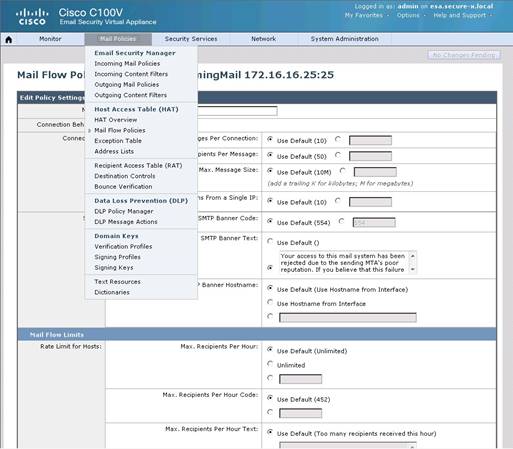














What is the maximum number of recipients per hour that the Cisco Email Security Appliance will accept from the green.public domain?
- A. 1
- B. 20
- C. 25
- D. 50
- E. 5000
- F. Unlimited
Answer: C
Explanation: From the instructions we know that the green.public domain has been assigned a reputation score of 2. From below we know that a reputation score of 2 belongs to the SUSPECTLIST, which has a policy of “THROTTLED”:
Capture
By clicking on the THROTTLED policy we see that the max recipients per hour has been set to 20: Capture
NEW QUESTION 5
Which IPS engine detects ARP spoofing?
- A. Atomic ARP Engine
- B. Service Generic Engine
- C. ARP Inspection Engine
- D. AICEngine
Answer: A
NEW QUESTION 6
Which three user roles are partially defined by default in Prime Security Manager? (Choose three.)
- A. networkoperator
- B. admin
- C. helpdesk
- D. securityoperator
- E. monitoringadmin
- F. systemadmin
Answer: BCF
NEW QUESTION 7
An engineer is deploying the Cisco Firepower NGIPSv for vMware. Which two aspects are unsupported during this deployment? (Choose two.)
- A. vCenter
- B. restoring a backup
- C. vCloud Director
- D. vMware tool
- E. cloning a virtual machine
Answer: AC
NEW QUESTION 8
What are two arguments that can be used with the show content-scan command in Cisco IOS software? (Choose two. )
- A. data
- B. session
- C. buffer
- D. statistics
- E. verbose
Answer: BD
NEW QUESTION 9
In which two places can thresholding settings be configured? (Choose two.)
- A. globally, per intrusion policy
- B. globally, within the network analysis policy
- C. on each access control rule
- D. on each IPS rule
- E. per preprocessor, within the network analysis policy
Answer: CD
NEW QUESTION 10
Which three statements about threat ratings are true? (Choose three.)
- A. A threat rating is equivalent to a risk rating that has been lowered by an alert rating.
- B. The largest threat rating from all actioned events is added to the risk rating.
- C. The smallest threat rating from all actioned events is subtracted from the risk rating.
- D. The alert rating for deny-attacker-inline is 45.
- E. Unmitigated events do not cause a threat rating modification.
- F. The threat rating for deny-attacker-inline is 50.
Answer: ADE
NEW QUESTION 11
Which three statements about Cisco ASACX are true? (Choose three.)
- A. It groups multiple ASAs as a single logical device.
- B. It can perform context-aware inspection.
- C. It provides high-density security services with high availability.
- D. It uses policy-based interface controls to inspect and forward TCP- and UDP-based packets.
- E. It can make context-aware decisions.
- F. It uses four cooperative architectural constructs to build the firewall.
Answer: BEF
NEW QUESTION 12
Which two configuration steps are required for implementing SSH for management access to a Cisco router? (Choose two.)
- A. Configuring the SSH version with the ip ssh version 2 command.
- B. Generating RSA key pairs with the crypto key generate rsa command.
- C. Enabling AAA for authentication, authorization, and accounting with the aaa new-model command.
- D. Enabling SSH transport with the transport input ssh command.
- E. Configuring a domain name with the ip domain-name [name] command.
Answer: DE
Explanation:
Reference: http://www.cisco.com/c/en/us/support/docs/security-vpn/secure-shell-ssh/4145ssh.html
NEW QUESTION 13
Which four parameters must be defined in an ISAKMP policy when creating an IPsec site-to-site VPN using the Cisco ASDM? (Choose four.)
- A. encryption algorithm
- B. hash algorithm
- C. authentication method
- D. IP address of remote IPsec peer
- E. D-H group
- F. perfect forward secrecy
Answer: ABCE
NEW QUESTION 14
What is retrospective alerting in Cisco Advanced Malware Protection for Endpoints?
- A. alerts when a file changes disposition
- B. alerts on events over a week old
- C. alerts showing previously installed malware
- D. alerts on previously blacklisted applications
Answer: C
NEW QUESTION 15
When you configure the Cisco ESA to perform blacklisting, what are two items you can disable to enhance performance? (Choose two.)
- A. rootkit detection
- B. spam scanning
- C. APT detection
- D. antivirus scanning
- E. URL filtering
Answer: BD
NEW QUESTION 16
Which IPS signature engine inspects the IP protocol packets and the Layer TCP?
- A. String TCP
- B. Atomic TCP
- C. Service HTTP
- D. Atomic IP
Answer: D
NEW QUESTION 17
Which Cisco ASA platform should be selected if the requirements are to support 35,000 connections per second, 600,000 maximum connections, and traffic shaping?
- A. A.5540B.5550C.5580-20D.5580-40
Answer:
NEW QUESTION 18
In order to set up HTTPS decryption on the Cisco Web Security Appliance, which two steps must be performed? (Choose two.)
- A. Enable and accept the EULA under Security Services > HTTPS Proxy.
- B. Upload a publicly signed server certificate.
- C. Configure or upload a certificate authority certificate.
- D. Enable HTTPS decryption in Web Security Manager > Access Policies.
Answer: AC
NEW QUESTION 19
Which four methods are used to deploy transparent mode traffic redirection? (Choose four.)
- A. PAC files
- B. Web Cache Communication Protocol
- C. policy-based routing
- D. Microsoft GPO
- E. Layer 4 switch
- F. DHCP server
- G. Layer 7 switch
- H. manual browser configuration
Answer: BCEG
P.S. Easily pass 300-210 Exam with 431 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 300-210 Dumps: https://www.certleader.com/300-210-dumps.html (431 New Questions)
