we provide Guaranteed Paloalto-Networks PCCET free practice questions which are the best for clearing PCCET test, and to get certified by Paloalto-Networks Palo Alto Networks Certified Cybersecurity Entry-level Technician. The PCCET Questions & Answers covers all the knowledge points of the real PCCET exam. Crack your Paloalto-Networks PCCET Exam with latest dumps, guaranteed!
Paloalto-Networks PCCET Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
- A. SaaS
- B. DaaS
- C. PaaS
- D. IaaS
Answer: D
NEW QUESTION 2
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
- A. is hardened against cyber attacks
- B. runs without any vulnerability issues
- C. runs within an operating system
- D. allows multiple, virtual (or guest) operating systems to run concurrently on a single physical host computer
Answer: CD
NEW QUESTION 3
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
- A. weaponization
- B. reconnaissance
- C. exploitation
- D. delivery
Answer: D
NEW QUESTION 4
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
- A. UDP
- B. MAC
- C. SNMP
- D. NFS
Answer: C
NEW QUESTION 5
DRAG DROP
Match the IoT connectivity description with the technology.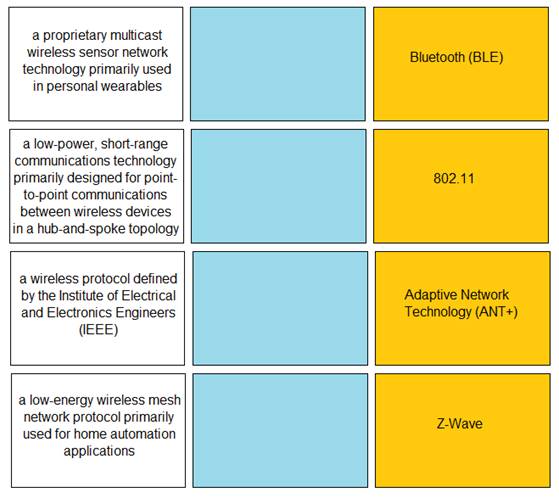
Solution:
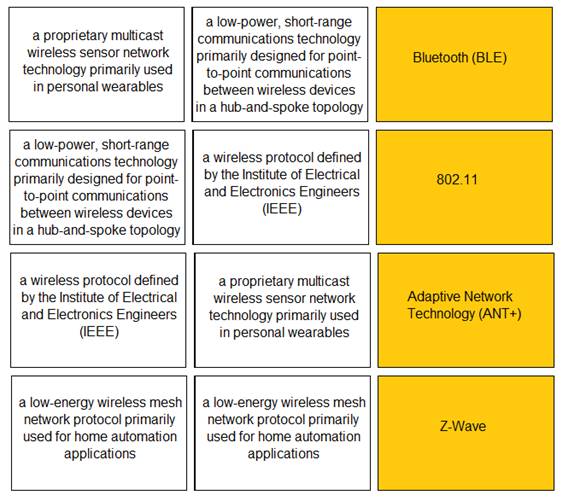
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
Which option describes the “selective network security virtualization” phase of incrementally
transforming data centers?
- A. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
- B. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
- C. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
- D. during the selective network security virtualization phase, all intra-host traffic is load balanced
Answer: A
NEW QUESTION 7
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
- A. North-South traffic
- B. Intrazone traffic
- C. East-West traffic
- D. Interzone traffic
Answer: A
NEW QUESTION 8
Which subnet does the host 192.168.19.36/27 belong?
- A. 192.168.19.0
- B. 192.168.19.16
- C. 192.168.19.64
- D. 192.168.19.32
Answer: D
NEW QUESTION 9
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
- A. Shortest Path
- B. Hop Count
- C. Split Horizon
- D. Path Vector
Answer: B
NEW QUESTION 10
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
- A. Computer
- B. Switch
- C. Infrastructure
- D. Cloud
Answer: C
NEW QUESTION 11
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
- A. operating system patches
- B. full-disk encryption
- C. periodic data backups
- D. endpoint-based firewall
Answer: B
NEW QUESTION 12
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. NetOps
- B. SecOps
- C. SecDevOps
- D. DevOps
Answer: B
NEW QUESTION 13
Which IPsec feature allows device traffic to go directly to the Internet?
- A. Split tunneling
- B. Diffie-Hellman groups
- C. d.Authentication Header (AH)
- D. IKE Security Association
Answer: A
NEW QUESTION 14
Which type of Wi-Fi attack depends on the victim initiating the connection?
- A. Evil twin
- B. Jasager
- C. Parager
- D. Mirai
Answer: B
NEW QUESTION 15
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
- A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
- B. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
- C. control and protect inter-host traffic by using IPv4 addressing
- D. control and protect inter-host traffic using physical network security appliances
Answer: D
NEW QUESTION 16
Which activities do local organization security policies cover for a SaaS application?
- A. how the data is backed up in one or more locations
- B. how the application can be used
- C. how the application processes the data
- D. how the application can transit the Internet
Answer: B
NEW QUESTION 17
Which tool supercharges security operations center (SOC) efficiency with the world’s most comprehensive operating platform for enterprise security?
- A. Prisma SAAS
- B. WildFire
- C. Cortex XDR
- D. Cortex XSOAR
Answer: D
NEW QUESTION 18
How does adopting a serverless model impact application development?
- A. costs more to develop application code because it uses more compute resources
- B. slows down the deployment of application code, but it improves the quality of code development
- C. reduces the operational overhead necessary to deploy application code
- D. prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
Answer: C
NEW QUESTION 19
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
- A. decrypt the infected file using base64
- B. alert system administrators
- C. quarantine the infected file
- D. delete the infected file
- E. remove the infected file’s extension
Answer: CDE
NEW QUESTION 20
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Dynamic
- B. Pre-exploit protection
- C. Bare-metal
- D. Static
Answer: A
NEW QUESTION 21
......
100% Valid and Newest Version PCCET Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/PCCET-dumps.html (New 75 Q&As)
