Printable of H12-711_V3.0 simulations materials and training tools for HUAWEI certification for candidates, Real Success Guaranteed with Updated H12-711_V3.0 pdf dumps vce Materials. 100% PASS HCIA-Security V3.0 exam Today!
Check H12-711_V3.0 free dumps before getting the full version:
NEW QUESTION 1
Which of the following are remote authentication methods? (multiple choice)
- A. RADIUS
- B. Local
- C. HWTACACS
- D. LLDP
Answer: AC
NEW QUESTION 2
In the Linux system, if the user wants to enter the tmp folder in the root directory, the command that needs to be entered is ______ /tmp.[fill in the blank]*
Solution:
cd
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
Drag the warning level of the network security emergency response on the left into the box on the right, and arrange it from top to bottom in order of severity.[fill in the blank]*
Solution:
3124
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
DHCP SnoopingWhich of the following attacks can be prevented? (multiple choice)
- A. DHCP ServerCounterfeiter Attack
- B. middleman withIP/MAC spoofingattack
- C. IPspoofing attack
- D. useoption82Phishing of fieldsDHCPlease renewal attack
Answer: ABCD
NEW QUESTION 5
Which of the following types of encryption technology can be divided into? (multiple choice)
- A. Symmetric encryption
- B. Symmetric encryption
- C. fingerprint encryption
- D. data encryption
Answer: AB
NEW QUESTION 6
Which of the following attacks is not a cyber attack?
- A. IP spoofing attack
- B. SmurfI attack
- C. MAC address spoofing attack
- D. ICMP attack
Answer: C
NEW QUESTION 7
Which of the following does not belong toLINUXoperating system?
- A. CentOS
- B. RedHat
- C. Ubuntu
- D. MAC OS
Answer: D
NEW QUESTION 8
againstIPspoofing attack (IP Spoofing), which of the following is an error?
- A. IPSpoofing attacks are based onIPaddress trust relationship to initiate
- B. IPAfter a successful spoofing attack, the attacker can use forged arbitraryIPThe address impersonates a legitimate host to access key information
- C. The attacker needs to put the sourceIPlandaddress masquerading as a trusted host and sendSYNmarkNote the data segment request connection
- D. based onIPThe hosts in the trust relationship of the addresses can log in directly without entering password authentication.
Answer: C
NEW QUESTION 9
The attacker sendsICMPAnswer the request and set the destination address of the request packet as the broadcast address of the victim network. What kind of attack is this behavior?
- A. IPspoofing attack
- B. Smurfattack
- C. ICMPredirect attack
- D. SYN floodattack
Answer: B
NEW QUESTION 10
As shown in the figure, the clientAand serverBestablished betweenTCPconnection, two places in the figure"?"The message sequence number should be which of the following?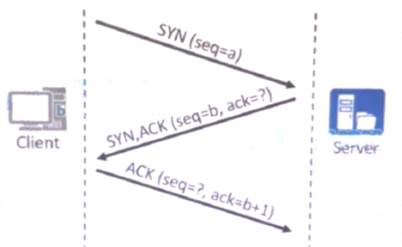
- A. a+1:a
- B. a:a+1
- C. b+1:b
- D. a+1:a+1
Answer: D
NEW QUESTION 11
Which of the following is used in digital signature technology to encrypt digital fingerprints?
- A. sender's public key
- B. sender private key
- C. Receiver's public key
- D. Receiver's private key
Answer: B
NEW QUESTION 12
Firewall in addition to supporting built-inPortalIn addition to authentication, it also supports customizationPortalauthentication, when using customPortalDuring authentication, there is no need to deploy externalPortalserver.
- A. True
- B. False
Answer: B
NEW QUESTION 13
Understanding engineering principles belongs to ( ) the category of security awareness training in information security prevention. (fill in the blank)
Solution:
Security
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 14
Which of the following security threats are terminal security threats? (multiple choice)
- A. man-in-the-middle attack
- B. There is a vulnerability in the server
- C. User identity is not verified
- D. Users use weak passwords
Answer: BCD
NEW QUESTION 15
The repair of anti-virus software only needs to repair some system files that were accidentally deleted when scanning and killing viruses to prevent the system from crashing
- A. True
- B. False
Answer: A
NEW QUESTION 16
In the classification of information security classified protection systems, which of the following levels define if an information system is compromised. Will it cause damage to social order and public interests? (
)[Multiple Choice Questions]
- A. The third level of security marking protection
- B. Level 4 Structural Protection
- C. Second-level system audit protection
- D. The first level of user self-protection
Answer: ABC
NEW QUESTION 17
Which of the following options is notUSG6000What file formats are supported by serial devices for saving certificates?
- A. PKCS#12
- B. DER
- C. PEM
- D. PKCS#
Answer: D
NEW QUESTION 18
......
P.S. Easily pass H12-711_V3.0 Exam with 492 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com H12-711_V3.0 Dumps: https://www.dumps-files.com/files/H12-711_V3.0/ (492 New Questions)
