we provide Downloadable HUAWEI H12-711_V3.0 torrent which are the best for clearing H12-711_V3.0 test, and to get certified by HUAWEI HCIA-Security V3.0. The H12-711_V3.0 Questions & Answers covers all the knowledge points of the real H12-711_V3.0 exam. Crack your HUAWEI H12-711_V3.0 Exam with latest dumps, guaranteed!
Also have H12-711_V3.0 free dumps questions for you:
NEW QUESTION 1
Regarding the description of vulnerability scanning, which of the following is false?
- A. Vulnerability scanning is a network-based technology for remotely monitoring the security performance vulnerabilities of target networks or hosts, and can be used to conduct simulated attack experiments and security audits.
- B. Vulnerability scanning is used to detect whether there are vulnerabilities in the target host system, generally scanning the target host for specific vulnerabilities
- C. Vulnerability scanning is a passive preventive measure that can effectively avoid hacker attacks
- D. can be based onpingScan and port scan results for vulnerability scanning
Answer: C
NEW QUESTION 2
Which of the following is false for a description of an intrusion detection system?.
- A. Intrusion detection system can collect a large amount of key information dynamically through network and computer.And can analyze and judge the current state of the entire system environment in time
- B. Once the intrusion detection system finds that there is a behavior that violates the security policy or the system has traces of being attacked, it can implement blocking operations.
- C. Intrusion detection system includes all hardware and software systems used for intrusion detection
- D. The immersion detection system can be linked with firewalls and switches, making it a powerful tool for firewalls"assistant", better and more precise control of traffic access between domains
Answer: C
NEW QUESTION 3
After a network intrusion event occurs, the identity of the intrusion, the source of the attack and other information are obtained according to the plan, and the intrusion behavior is blocked. The above actions belong to PDRR. What are the links in the network security model? (multiple choice)
- A. Protection link
- B. Detection link
- C. response link
- D. recovery link
Answer: BC
NEW QUESTION 4
When dual-system hot backup is deployed on the firewall,VRRPWhich of the following protocols should be used to switch the overall status of a backup group?
- A. VRRP
- B. VGMP
- C. HRP
- D. OSPF
Answer: B
NEW QUESTION 5
If internal employees access the Internet through the firewall and find that they cannot connect to the Internet normally, what viewing commands can be used on the firewall to troubleshoot the interface, security zone, security policy and routing table? (Write any viewing command, requiring: the words on the command line must be complete and correct to score, and cannot be omitted or abbreviated)[fill in the blank]*
Solution:
display zone display current-configurationdisplay ip routing-tabledisplay security-policy rule alldisplay ip interface brief)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
in configurationNATDuring the process, in which of the following situations, the device will generateServer-maptable entry? (multiple choice)
- A. configuration sourceNATautomatically generated whenserver-mapentry
- B. configureNATserverAfter success, the device will automatically generateServer-mapentry
- C. configureeasy-ipwill be generated whenserver-mapentry
- D. configureNAT No-PATAfter that, the device will establish a data stream for the configured multi-channel protocolserver-mapsurface
Answer: BD
NEW QUESTION 7
In a stateful inspection firewall, when the stateful inspection mechanism is enabled, the second packet of the three-way handshake (SYN+ACK) when reaching the firewall, which of the following descriptions is correct if there is no corresponding session table on the firewall?
- A. The firewall does not create a session table, but allows packets to pass through
- B. If the firewall security policy allows packets to pass, create a session table
- C. Packets must not pass through the firewall
- D. Packets must pass through the firewall and establish a session
Answer: C
NEW QUESTION 8
During the process of establishing IPSec VPN between peers FW_A and FW_B, two types of security associations need to be established in two stages. In the first stage, ______ is established to verify the identity of the peers.[fill in the blank]*
Solution:
IKE SA
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
When A and B communicate with each other in data communication, if an asymmetric encryption algorithm is used for encryption, when A sends data to B, which of the following keys will be used for data encryption?
- A. A's public key
- B. A's private key
- C. B's public key
- D. B's private key
Answer: C
NEW QUESTION 10
Which of the following is network address port translation (NAPT) and only translate network addresses (No-PAT) difference?
- A. go throughNo-PATAfter conversion, for external network users, all packets come from the sameIPaddress
- B. No-PATOnly supports protocol port translation at the transport layer
- C. NAPTOnly supports protocol address translation at the network layer
- D. No-PATSupports protocol address translation at the network layer
Answer: D
NEW QUESTION 11
According to the management specification, regularly check the network security system and equipment, upgrade the patch, and organize the network security emergency response drill. The above actions belong toMPDRRWhat are the elements of the network security model?
- A. Protection link
- B. Detection link
- C. response link
- D. Management link
Answer: BC
NEW QUESTION 12
Regarding the NAT policy processing flow, which of the following options are correct? ( )*
- A. Server-map is processed before the security policy is matched
- B. Source NAT policy is processed after security policy match
- C. Source NAT policy queries are processed after the session is created
- D. Server-map is processed after state detection
Answer: ABD
NEW QUESTION 13
Which of the following is true about the security policy configuration command?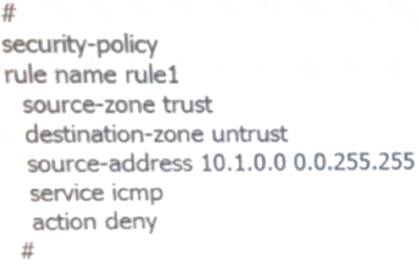
- A. prohibited fromtrustRegional accessuntrustarea and the destination address is 10.1.10.10hostICMPmessage
- B. prohibited fromtrustRegional accessuntrustarea and the destination address is10.1.0.0/16All hosts on the segmentICMPmessage
- C. prohibited fromtrustRegional accessuntrustregion and the source address is10.1.0.0/16All hosts from the network segmentICMPmessage
- D. prohibited fromtrustRegional accessuntrustregion and the source address is10.2.10.10All hosts from hostICMPmessage
Answer: C
NEW QUESTION 14
SNMPWhat versions of the protocol are there? (multiple choice)
- A. SNMPv1
- B. SNMPv2b
- C. SNMPv2c
- D. SNMPv3
Answer: ACD
NEW QUESTION 15
When the company's network administrator is performing dual-system hot backup, due to the possibility of inconsistent round-trip paths, if he wants to enable the session fast backup function, the command that needs to be entered is _______ [fill in the blank]*
Solution:
hrp mirror session enable
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
When connecting in a public placeWi-FiWhich of the following actions is relatively safer?
- A. The connection is not encryptedWi-Fihot spot
- B. Connection is paid by the operatorWi-FiHotspot and web browsing only
- C. connect unencrypted for freeWi-Fimake online shopping
- D. Connection encrypted for freeWi-FiPerform online transfer operations
Answer: B
NEW QUESTION 17
( ) Can block discovered network intrusions in real time. (fill in the blank)
Solution:
Firewall
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 18
......
Recommend!! Get the Full H12-711_V3.0 dumps in VCE and PDF From Allfreedumps.com, Welcome to Download: https://www.allfreedumps.com/H12-711_V3.0-dumps.html (New 492 Q&As Version)
