Proper study guides for Regenerate HUAWEI HCIA-Security V3.0 certified begins with HUAWEI H12-711_V3.0 preparation products which designed to deliver the Top Quality H12-711_V3.0 questions by making you pass the H12-711_V3.0 test at your first time. Try the free H12-711_V3.0 demo right now.
Also have H12-711_V3.0 free dumps questions for you:
NEW QUESTION 1
Which of the following descriptions about the DNS protocol is correct?
- A. There are four types of servers in the DNS domain name resolution system: root server, top-level domain name server, recursive server and cache server.
- B. The DNS protocol port number is 53
- C. DNS protocol transport layer can use either TCP or UDP
- D. If the DNS cache server does not have the domain name resolution cache to be queried, it will directly query the top-level domain name server
Answer: ABD
NEW QUESTION 2
HTTPmessage usageUDPcarry, andHTTPSprotocol based onTCPthree-way handshake, soHTTPSSafer and more recommendedHTTPS.
- A. True
- B. False
Answer: B
NEW QUESTION 3
When configuring user single sign-on, if you use the mode of querying the AD server security log, please check the followingcertifiedProcedureEnterRow ordering:[fill in the blank]*
The AD monitor forwards the user login message to F7, and the user goes online at F7.
AD monitor through the WMI interface provided by AD server. Connect to the AD server to query the security log. Get the user login message.
accessboardrecord AD domain, AD servicedevicerecorduseHouseholdsuperiorStringinformation into the security log.
The AD monitor starts from the time when the AD single sign-on service starts, and regularly queries the security logs generated on the AD server.
- A.
Answer: 4213
NEW QUESTION 4
want to implement security policy"Anti-virus function", must beLicenseactivation.
- A. True
- B. False
Answer: A
NEW QUESTION 5
Please order the following steps according to the graded protection process.[fill in the blank]
Solution:
grading, filing, testingComment,rectification, supervision)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
Which of the following NAT technologies is a destination NAT technology?
- A. Easy-ip
- B. NAT No-PAT
- C. NAPT
- D. NAT Server
Answer: D
NEW QUESTION 7
Execute the command on the firewall and display the above information. Which of the following descriptions is correct? (multiple choice)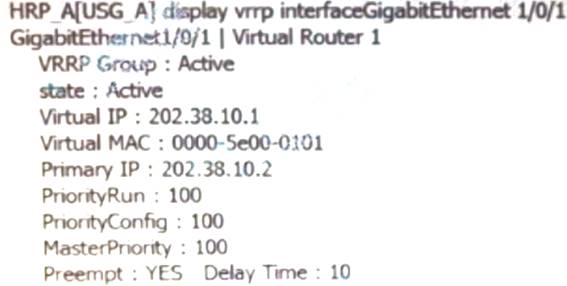
- A. this firewallVGMPgroup status isActive
- B. this firewallG1/0/1virtual interfaceIPaddress is202.38.10.2
- C. this firewallVRIDfor1ofVRRPThe priority of the backup group is100
- D. When the main deviceUSG_AWill not switch in the event of a failure
Answer: ABC
NEW QUESTION 8
deployIPSec VPNIn tunnel mode, useAHprotocol for packet encapsulation. NewIPIn the header field of the packet, which of the following parameters does not need to be checked for data integrity?
- A. sourceIPaddress
- B. PurposeIPaddress
- C. TTL
- D. Identification
Answer: C
NEW QUESTION 9
Business Impact Analysis (BIA) does not include which of the following?
- A. business priority
- B. Incident handling priority
- C. impact assessment
- D. Risk Identification
Answer: C
NEW QUESTION 10
Which of the following options is correct regarding the description of firewall hot standby? (multiple choice)
- A. When the dual-system backup function needs to be provided in multiple areas on the firewall, it is necessary to configure multipleVRRPbackup group
- B. require the same firewall on the sameVGMPmanagement group ownedVRRPBackup group status remains consistent
- C. Firewall dual-system hot backup requires session table,MACInformation such as tables and routing tables are synchronized and backed up between the master device and the slave device
- D. VGMPto guarantee allVRRPConsistency of backup group switching
Answer: ABD
NEW QUESTION 11
aboutSSL VPNTechnology, which of the following statements is false?
- A. SSL VPNtechnology can be perfectly adapted toNATthrough the scene
- B. SSL VPNThe encryption of the technology only takes effect at the application layer
- C. SSL VPNRequires a dial-up client
- D. SSL VPNTechnology expands the reach of the enterprise's network
Answer: C
NEW QUESTION 12
IPSec VPNAn asymmetric encryption algorithm is used to encrypt the transmitted data
- A. True
- B. False
Answer: B
NEW QUESTION 13
VGMPIn which of the following situations occurs in the group, the group will not actively send the message to the peerVGMPmessage/
- A. Dual-system hot backup function enabled
- B. Manually switch the active and standby status of the firewall
- C. Firewall service interface failure
- D. Session table entry changes
Answer: D
NEW QUESTION 14
- A. this firewallVGMPgroup status isActive
- B. this firewallG1/0/0andG1/0/1interfaceVRRPgroup status isstandby
- C. this firewallHRPThe heartbeat line interface isG1/0/0andG1/0/1
- D. This firewall must be in preemptive state
Answer: B
NEW QUESTION 15
For network security incidents that occur, remote emergency response is generally adopted first. If the problem cannot be solved for the customer through remote access, after confirmation by the customer, go to the local emergency response process
- A. True
- B. False
Answer: A
NEW QUESTION 16
Which of the following is true about the difference between pre-incident prevention strategies and post-incident recovery strategies? (multiple choice)
- A. Prevention strategies focus on minimizing the likelihood of an accident before a story occur
- B. Recovery strategies focus on minimizing the impact and damage to the business after an incident
- C. The role of pre-disaster prevention strategies does not include minimizing economic and reputational losses caused by accidents
- D. Recovery strategies are used to improve business high availability
- E. A recovery strategy is part of a business continuity plan
Answer: ACD
NEW QUESTION 17
Please match the following malicious code categories and descriptions[fill in the blank]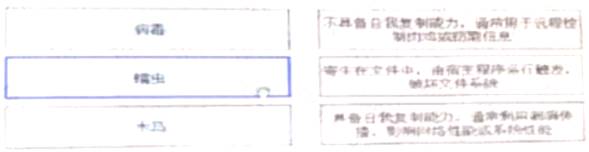
Solution:
Virus: parasitic in the file, starts from the host program, destroys the file system: worm: has the ability to self-replicate and usually uses loopholes to spread to affect network performance or system performance: Trojan horse: does not have the ability to self-replicate, usually used to remotely control broilers or stealing information)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 18
......
Recommend!! Get the Full H12-711_V3.0 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/H12-711_V3.0-dumps.html (New 492 Q&As Version)
